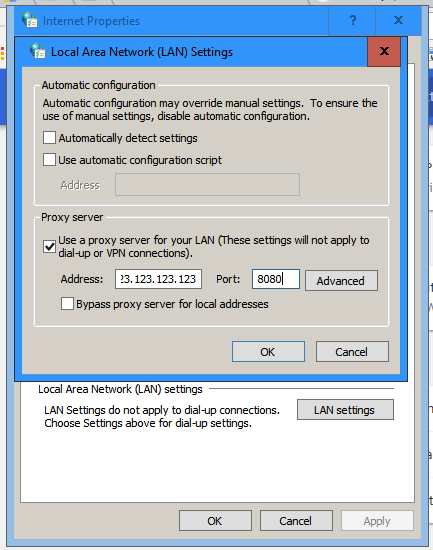
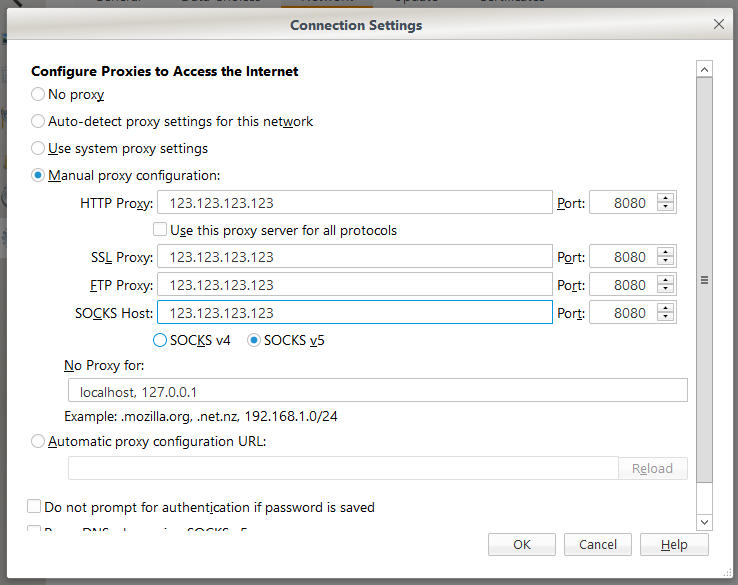
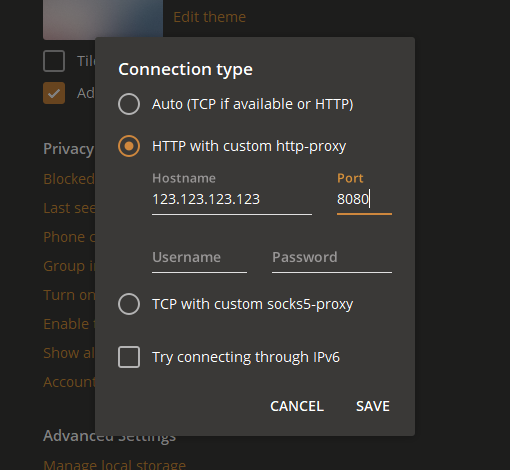
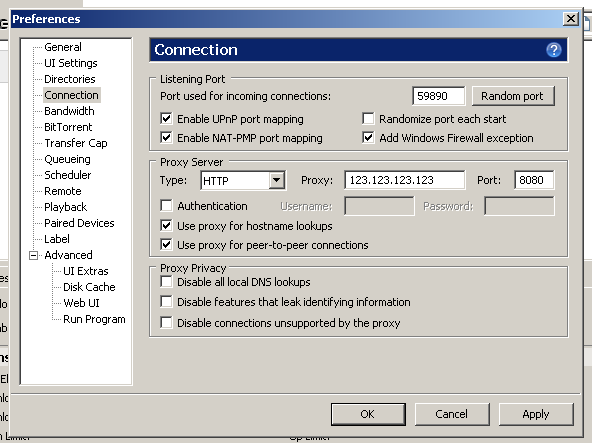
There are only two types of proxy protocols – HTTP (Hypertext Transfer Protocol) proxies and SOCKS (Secure Socket) proxies. Although they are similar in that they both route internet traffic through a remote server, they operate very differently from each other and because of that also have very different uses.
If you’re currently looking to buy proxies online, or have been using proxies from websites that provide them for free, you have no doubt noticed most proxy providers have HTTP or HTTPS Proxies and only a select few have SOCKS proxies. So what is the difference, and does it matter?
If all this HTTP and SOCKS talk is already too confusing, click here to learn more about what a proxy server actually does. Otherwise, continue reading below to have HTTP vs SOCKS proxies explained!
Understanding the HTTP Protocol and HTTP Requests
The industry standard for proxies is the HTTP protocol – that’s because the entire internet runs on the HTTP protocol and why every URL of a website begins with “http://” (even if modern web-browsers add that part for you these days). You see the HTTP protocol every day and probably just don’t notice it, or you even block it out completely because it’s second-nature by now.
The HTTP Protocol functionality works via a request-response basis on a client-server setup. Generally, the “client” in this scenario is a web-browser that sends out a request for information to a remote server. The client sends the “HTTP request” as a URL (Uniform Resource Locator). The “server” in this example will generally be a computer running a website-serving application known as a web-server, or some other web-based application. When the server receives the HTTP request from the client, it will send back whatever resources the client requested, which could be anything from an image, a document, or even a web page.
So when you open up a browser like Chrome and type in “google.com” in the URL bar, the browser adds “http://” to it and then sends an HTTP request to http://google.com servers requesting whatever it is they have for users at the “google.com” location, which is a web page. The HTTP protocol is how you are requesting the information, and the HTTP protocol is how it’s being sent back to you.
How HTTP and SOCKS Proxies Function Differently
How HTTP Proxies Function
HTTP Proxies were specifically designed with the HTTP protocol meant as their means of operation. HTTP Proxies were made to be used over the HTTP protocol to request and receive information within it’s limits while using the same network ports that the HTTP protocol uses.
Because of this, HTTP proxies are the most prevalent of the two kinds of proxies and are most often the kind people use.
How SOCKS Proxies Function
SOCKS proxies function differently than HTTP proxies, some refer to SOCKS proxies as operating on a “lower level”. Since HTTP were designed with the HTTP Protocol in mind, they are tailored to work with it, and only it. However, SOCKS proxies can work over any network protocol on any network port.
Basically, this means SOCKS proxies are more versatile and can be used by various applications.
HTTP Proxy Security Vs. SOCKS Proxy Security
HTTP Proxy Security Overview
Generally speaking, HTTP proxies are not as secure as SOCKS proxies. It doesn’t matter if the HTTP Proxy is public, private, dedicate, or shared – All HTTP Proxies are less secure than a SOCKS proxy.
Because HTTP Proxies are designed to operate on HTTP protocol connections, the “smarter” HTTP proxy server can see and understand any traffic being sent through it. Therefore, HTTP proxies are only as secure and private as the operator of the server wants them to be. An HTTP proxy provider could, potentially, track everything you do through their proxy server and submit logs to law enforcement or other government agencies.
However, and this is a big “however”, there is a thing called HTTPS proxies and the “S” stands for “Secure”. HTTPS proxies use the CONNECT method to make secure tunnels between a client and server.
SOCKS Proxy Security Overview
SOCKS proxies, on the other hand, being “dumb”, low-level, proxies can not interpret or even understand the data moving to or from the client and server.
Technically, SOCKS proxies make secure tunnels like HTTPS proxies, but SOCKS proxy tunnels are TCP/IP based and are just established via the proxy rather than operating through it. Instead of the proxy acting as a middle-man, the way HTTP proxies behave, SOCKS proxies make direct connections using a “handshake” for permission to open the secure tunnel.
SOCKS proxies come in two variations – SOCKS version 4 and SOCKS version 5. SOCKS5 is newer and has added support for UDP traffic and extra security, but for most uses a SOCKS4 will do fine.
Conclusion of HTTP Proxy and SOCKS Proxy Differences
Since SOCKS proxies and HTTP proxies run on the same kind of hardware, for the most part they have the same speeds and stability as each other. The main factor in both HTTP and SOCKS Proxy performance depends on who is hosting them, what kind of hardware they are running on, and how much bandwidth they have. If a crappy proxy provider hosts their HTTP proxies on mediocre servers with low bandwidth, chances are their SOCKS proxies will suck too. If a proxy provider is serious, their servers will be in high-tech data-centers with at least 100Mb to 1GB+ connections, and your HTTP/SOCKS proxy speeds and stability will only be hindered by how many people you are sharing proxy servers with.
There are two flavors of proxies sold online – shared and dedicated. Shared Proxies are proxies that are accessible by multiple users that the proxy provider is selling to, and Dedicated proxies are accessible by only one user. If you need constantly high-performing proxies, go with dedicated proxies. If you are using proxies to access websites and services that like to ban IP addresses that are abusive, go with dedicated proxies. If you just need to make lots of connections from different IP addresses, performance doesn’t really matter, and it’s okay if some IPs get blocked – then shared proxies are definitely the way to go. (Learn more about shared and dedicated proxies here.)
As for when to use HTTP proxies versus SOCKS proxies, it really depends on what the proxy is being used for. If you are using proxies in a web-browser to access websites, then HTTP proxies are right for you. If you are using proxies for applications other than web-browsers to access things on the web that aren’t websites, like game servers or torrenting, then SOCKS proxies are generally what you will need to use.